With the increase in dependence on it in all fields, the Internet has spread dramatically in the last decade. There is almost no home in the world without at least one internet user. According to the “We Are Social” report, issued in cooperation with the Hootsuite Marketing Research Foundation, the number of Internet users in the world reached 4.54 billion in January of 2020, an increase of 298 million users over the year 2019. More than 60 percent of the world’s population Are connected to the Internet.
Online privacy is a growing concern among internet surfers. In a January 2019 Panda Security survey, 53% of online users said they were more concerned about their online privacy this year than they were last year.
With this growing concern, what is Tor Browser? How safe is it? What are its uses? How can the Tor Browser protect your privacy on the Internet? This is a complete guide about the browser that will be the star of the coming years.
Read also:
لفك الحظر عن المواقع والألعاب، ما هو الـ VPN؟ وما هي أفضل خدمات الـ VPN الآمنة؟
an introduction
Most of the sites collect data about their visitors, their IP addresses, their browsers and devices, their comments on the site’s articles and their e-mail if they placed it, and the URL of the site that referred you to them. This could evolve into how you use the site and how you look and feel about it. In fact, as you are reading the article now, we are collecting this information about you. Do not worry. We collect this information only for the purpose of improving the site. See our privacy policy .
In fact, even your ISP knows everything about you. Concerns are growing about what websites, internet providers, and governments can know about individuals on the Internet. This information is of great importance for websites to help them improve the website experience and improve the effectiveness of their advertising campaigns and their targeting of the audience. This information is of interest to governments to monitor and track criminals and violations on the Internet. But there are also many concerns. The concerns are that sites or internet providers are sharing this data with or even selling to third parties. Or governments use this data to prosecute human rights activists or independent journalists.
The use of VPN software may be a safe haven for many. But it really isn’t. Some VPN companies record your history while using their service. They may collect, store or share any information about you (they should review their usage policy). Many companies collaborate with governments to provide information about government-tracked VPN users.

What is Tor Browser?
The Tor Project
It is a non-profit organization that was established in 2006. The organization’s interest is focused on research and development in the field of privacy and anonymity on the Internet. The organization says it “struggles every day to ensure that everyone has private, unsupervised access to the Internet.” And it adheres ” strongly to transparency and user safety.” Of her browser, she says, ” Tor is more than just a program. It’s a loving work produced by an international community of people devoted to human rights.” Many researchers and developers work on the Tor Project “united by a common belief: Internet users should have exclusive access to an uncensored web.” It also describes the project itself.
Tor Browser
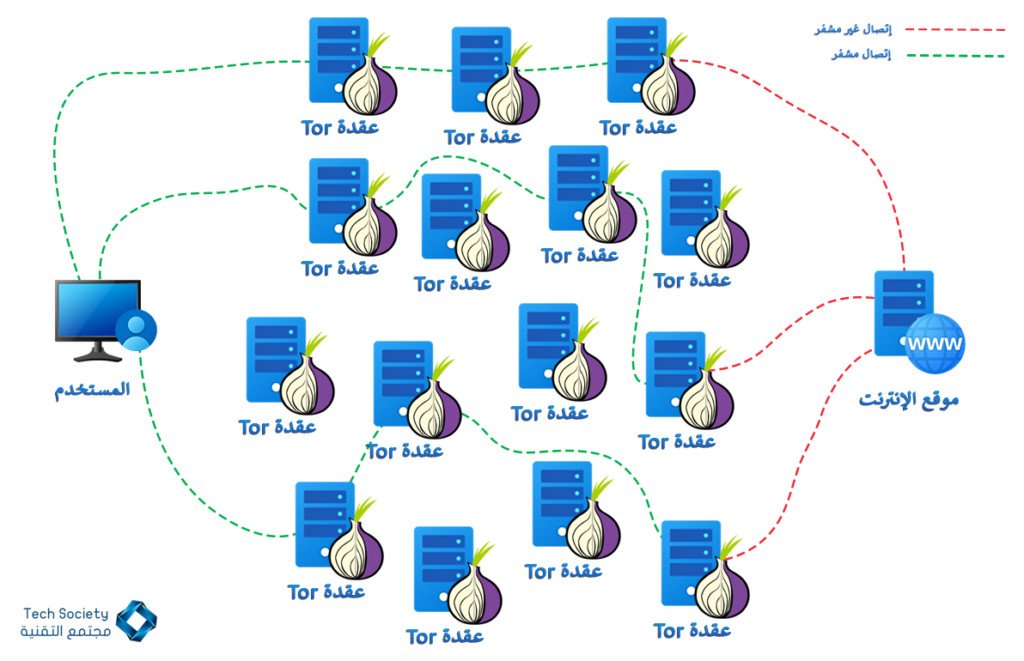
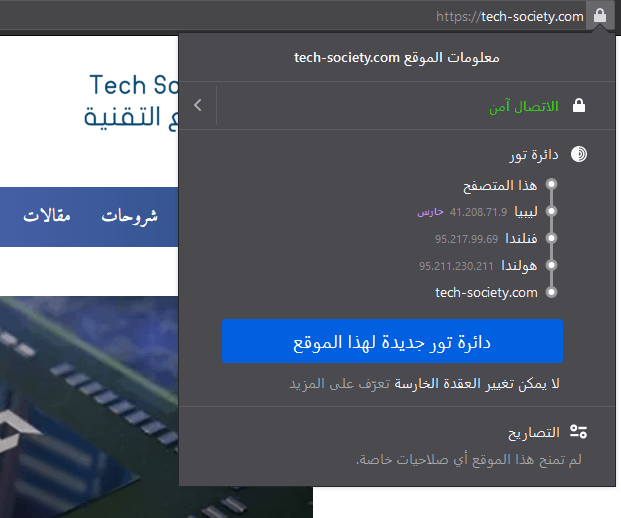
Tor Browser shortly “The onion router” is an open source web browser that anonymizes your web traffic using the Tor network, making it easy to protect your identity online. Some major web services block Tor users. Tor Browser is also illegal in some countries with authoritarian regimes that want to prevent citizens from reading, posting, and communicating without revealing their identity.
Tor Browser is available for all computers with Windows, OS X and Linux, as well as for Android phones. The browser is available in more than 30 languages, including Arabic. You can download it from here .
Tor Network
In 1995, two researchers at the United States Naval Research Laboratory (NRL) created and published the first research designs and prototypes for what he called “onion routing”. The aim of the onion directive was to obtain a way to use the Internet with the greatest possible privacy so that no observer or tracker of the network could discover the activities of users on it, and the idea was to direct traffic through multiple servers and encrypt it every step of the way.
Since its inception in the 1990s, the onion routing has been designed to be based on a decentralized network. The network needed to be operated by entities of diverse interests and trust, and the software should be free and open source to achieve maximum transparency. That’s why in October 2002 when the Tor Network was first published, its code was released with a free and open software license. By the end of 2003, the network had about 12 volunteer contracts, most of them in the United States.






إترك رد